How Your Social Media Activity Can Make You a Sitting Duck

For many companies, social media is a powerful marketing and recruiting tool, fostering brand awareness and connection to current and potential customers. For a small business with limited resources, social media can function as an inexpensive advertising mechanism to a wide-ranging audience.
It’s also a highly engaged audience with the average global user spending 2 hours and 36 minutes a day on social media sites in 2018, according to statista.
But, have you considered that the information your company posts to social media can also make it an easy target for cybercriminals?
THE PROBLEM
The personal privacy risks associated with oversharing on social media is generally accepted by the typical user, whether or not they act accordingly. But companies also put themselves at risk by providing seemingly safe corporate information on a regular basis to their social media feeds in the interest of having an online presence.
As corporate social media use increasingly looks like mainstream personal use, the same security concerns are brought into play. Posting photos of your events at your office could inadvertently reveal clues that could be used to social engineer an employee or expose a security weakness. Posting updates from your company’s annual trip alerts criminals that your office is empty or is operating with a skeleton staff.
And, it’s not just the posts on your company’s page that can be mined for data. The interrelated nature of social media makes the personal accounts of your employees valuable as additional sources of information as well as potential sources of entry to your network.
Likewise, vendors and partners who are linked to or follow and comment on your social media accounts represent another attack vector, especially if they have a poor cybersecurity profile.
HOW COMPANIES GET HACKED
If you think like a hacker, you know that trying to hack past a company’s firewall and compromise highly guarded information without being detected is much harder than developing customized social engineering campaigns using the information you can find easily on social media sites.
People are wired to want to connect, which makes social media so appealing to us and so productive for cybercriminals. People’s willingness to share combined with the trust-based nature of social media is why phishing campaigns are more successful on this platform than via email.
Further, statista found that 81% of social media traffic in the third quarter of 2019 came from mobile. That’s important because the user interface on mobile can make users more likely to fall for phishing scams.
So, what methods are cybercriminals using on social media to infiltrate your network?
· According to FireEye, email is the vehicle used in 91% of cybercrime. The personal information that is common on social media makes it much easier to impersonate another employee or senior management.
· Malicious links are more effective on social media, where people are less suspicious than they are with email links. Hackers can pose as someone you know and send malicious links through direct messages.
· Fake accounts can be created using photos and details of actual people or companies to create real-looking, but fake profiles to attract connections and distribute malware.
· Similarly, profile hacking, like the August 2019 hack of Jack Dorsey’s twitter account, are generally undertaken to embarrass people or companies and damage their reputation.
· Old social media accounts, that still exist but are neglected, present an easier opportunity for profile hacking than active accounts and could be used for illegal activity under the guise of your company.
· Shortened URLs, such as those from Ow.ly and Bitly, can easily hide malicious links.
· Hackers can pose as a customer service employee of any of the social media platforms and send an email that your account has been cancelled or compromised. Reinstating the account requires you to input your information.
· Social media quizzes are a way for hackers to acquire personal information that can be used to socially engineer you or your friends.
· Social media accounts are easily accessed on mobile devices, which makes them easy to compromise if a hacker gains possession of a lost or stolen employee device.
HOW TO PROTECT YOUR COMPANY & EMPLOYEES
First, be clear on why your company needs a social media presence. Maybe it doesn’t. That’s a tough sell, especially to a new or small business, but companies were able to grow for years before social media existed.
Nonetheless, if your company does maintain social media accounts, know which channels you’re on and which employees have administrative access.
Most importantly, have a social media policy that lays out what is and isn’t acceptable to post about the company. Then, train employees on how their personal use of social media can be detrimental to them and the company. Some general best practices include:
· Use two-factor authentication.
· Don’t connect with people you don’t know.
· Don’t click on questionable links in social media posts. Instead, type the URL into your browser to view.
· Don’t share information about yourself or the company that could be the answer to security questions used to identify you.
· Don’t use the same password across platforms or for business purposes.
· Utilize the privacy settings on each platform.
· Don’t access your personal accounts or the company’s accounts over public Wi-Fi.
· Report any suspicious activity immediately.
MONEY TALKS…
So, you know what walks, right? It’s understood that there’s a tradeoff between free social media and complete privacy and most are willing to make the exchange. However, the amount of privacy that’s relinquished tends to be more than people anticipate or understand. For social media companies, the business model is to generate revenue by selling your personal information to advertisers. So, it’s in the best interest of these companies (and their shareholders) to encourage you to provide plenty of identifiable data about yourself.
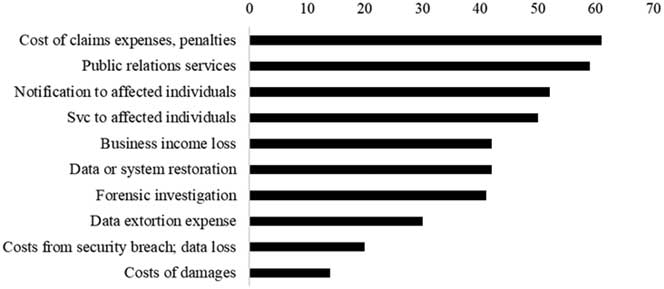
It’s in the best interests of cyber-scammers too, who have created a $3+ billion social media crime industry using the data they collect from these sites.